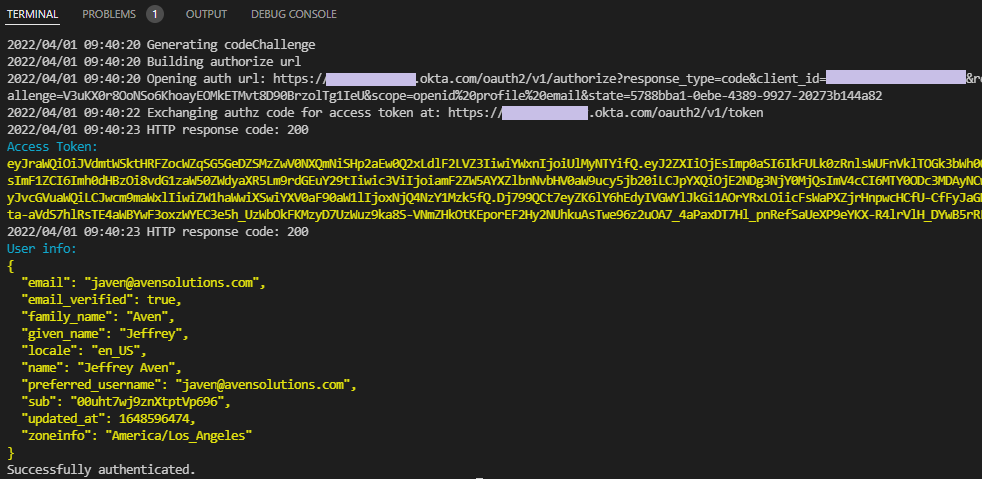
This article demonstrates a simple command line utility to login to an authorization server (Okta in this case) using a PKCE (Proof Key for Code Exchange) flow. This is the preferred flow for public clients (such as Single Page Applications).
The code for this article is available on GitHub
Example
Overview
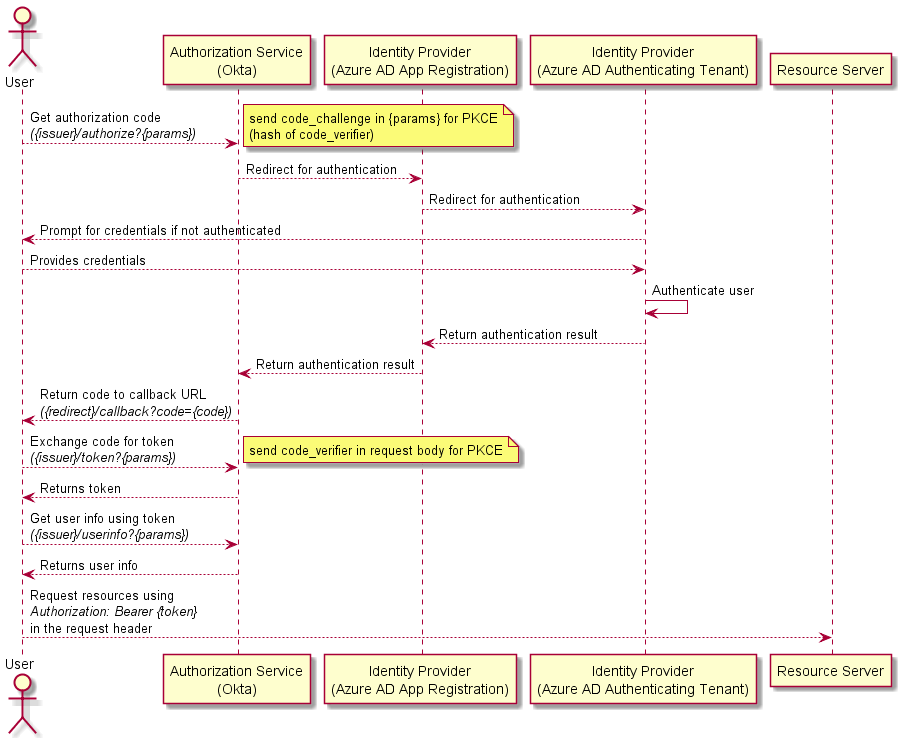
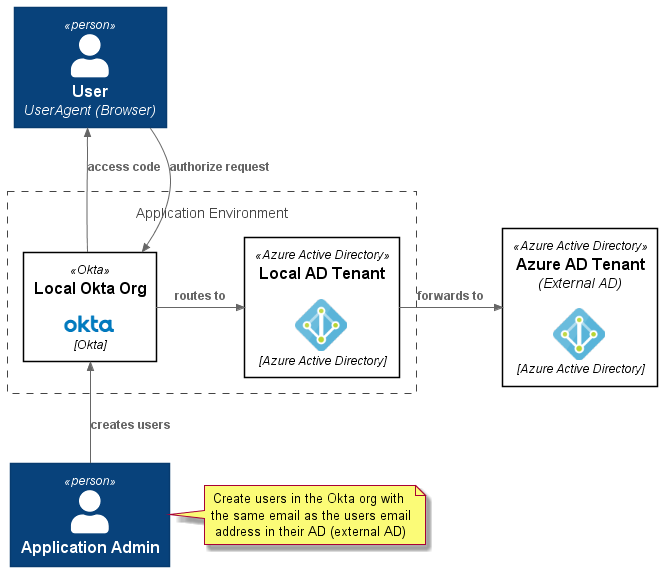
This application can be used to illustrate the authorization/authentication flow discussed in Simple SSO with an external IdP using Active Directory and Okta. A flow which is pictured here:
Steps
The steps involved in the implementation of a PKCE login flow are as follows:
Generate a code_challenge
To implement a PKCE flow, you first need to generate a Code Verifier (which is a random value you create), the Code Verifier is then hashed using a SHA256 algorithm. The hash is then used as the Code Challenge. An example function to generate a code challenge is shown below:
For more information see Use PKCE to Make Your Apps More Secure.
Build the authorize url
The authorize url is used to initiate the authorization flow with the authorization server. An example function to construct the authorize url is shown below:
Get the authorization code via redirect uri
The redirecturi parameter supplied in the authorize url is used to retrieve the authorization code from the authorization server. In order to get this code using a front end flow, you need to define a handler that will get the authorization code, call the token endpoint, and close the HTTP server, as shown here:
Exchange the code for an access token
The access token is what you ultimatly want, as this is the token that will be used to access protected resources. An example function to exchange the authorization code for an access token is shown below:
(Optional) Get the user profile
The access token can be used to get the user profile, this is done by calling the userinfo endpoint using the token. An example function to get the user profile is shown below:
with inspiration from...
- Auth0 PKCE flow for a CLI built in golang
- Golang sample for a CLI obtaining an access token using the PKCE flow
- oktadev/okta-node-cli-example
- Build a Command Line Application with Node.js
- About the Authorization Code grant with PKCE
if you have enjoyed this post, please consider buying me a coffee ☕ to help me keep writing!